OSI layer model
Divided into 7 layers, the various protocols are classified according to their tasks and functions.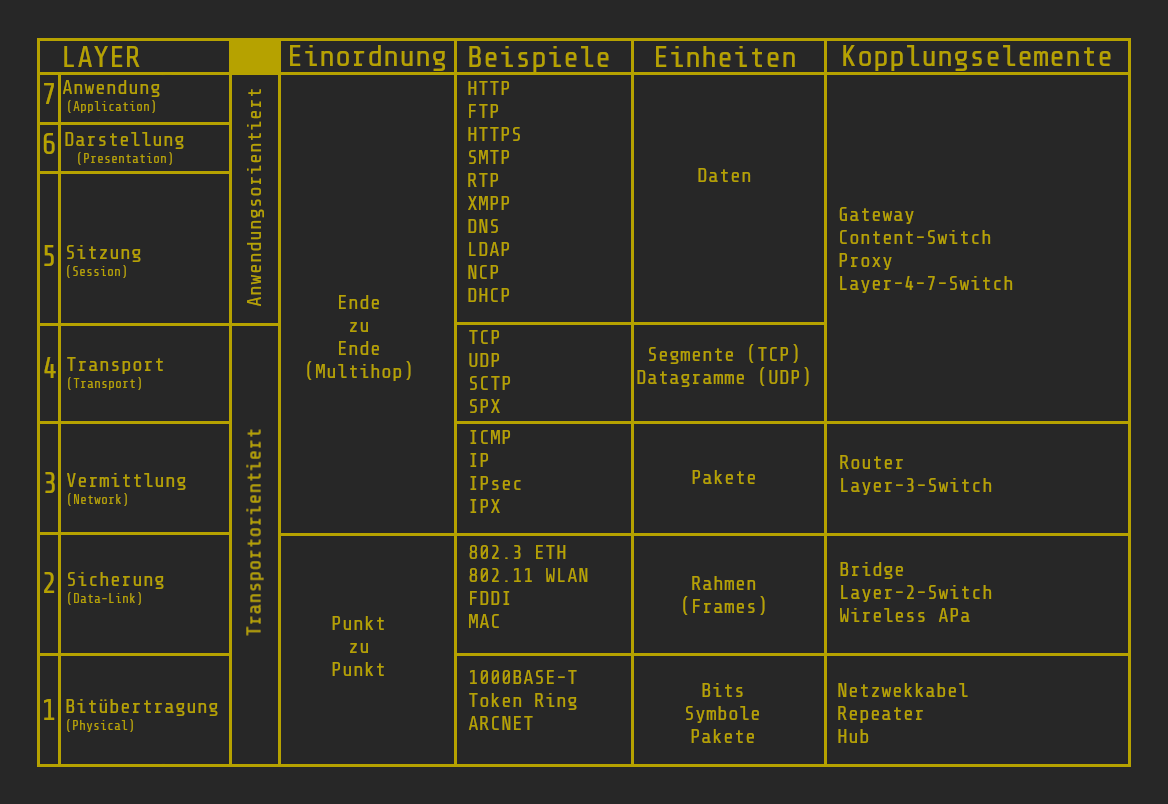
In networks, clients are provided with various services of different types. In order to ensure communication between both clients, a large number of tasks must be handled in terms of reliability, security, efficiency, etc. Starting with a simple signal through to complex processing in applications. Due to the large number of tasks, the OSI model was introduced and divided into seven layers. The requirements are implemented separately on each individual layer. The instances on both sides (sender and receiver) must work according to the same fixed rules. These rules are recorded as a protocol and are defined by the logical horizontal connection of two instances in a layer. Each instance provides services that the instance above can use. The real data flow therefore takes place vertically.
Layer-1 (Physical Layer)
Layer 1 is the lowest layer. This layer provides the physical components for mechanical, electrical or other types of data transmission. It activates, maintains or deactivates the connections and transmits bits over them. The type of signals ranges from sound to electromagnetic waves, optical signals to electrical signals. Devices or network components that belong to Layer 1 include:- Antennas
- Amplifiers
- Plug/socket for network cables
- Repeaters
- Hub
- Transceivers
In Layer 1 it must also be defined how the bits are to be transmitted (bit or symbol sequences, waves, etc.) and the coding must also be defined in the 1st layer.
Layer-2 (data link)
Layer-2 takes care of the largely error-free transmission of data and regulates access to the transmission medium. Here, bit streams are divided into blocks (frames) and checksums are assigned to the blocks so that the receiver can discard or correct faulty blocks. The data flow control in layer-2 allows the receiver to control the speed at which the other side can send its blocks. Hardware used in this layer includes bridges and switches (multiport bridges).Layer-3 (network layer)
Layer-3 takes care of switching connections (for performance-oriented services) and forwarding packets (for packet-oriented services). The data transmission takes place over the entire communication network, including routing between the network nodes. If the sender and receiver are not directly connected to each other, the packets are passed on at the same layer and do not reach upper layers. This happens from node to node until the recipient is reached. The network layer also takes care of the provision of cross-network addresses, the associated routing and the creation and updating of routing tables. This is why the Internet Protocol (IP) and NSAP addresses are also found here, as these are needed to ensure routing. On the hardware side, Layer 3 is handled by routers and Layer 3 switches.Layer-4 (Transport Layer)
Layer-4 ensures the segmentation of the data stream or its division to ensure a constant data stream. Layer-4 also provides uniform access to data streams for Layer-5 to Layer-7.Layer-5 (Session Layer)
This layer takes over the control of logical connections, i.e. it takes care of the process communication between two connections. This results in a stable connection that is implemented using fixed points. At these fixed points, a session can be synchronized again after the failure of a transport connection without having to start from the beginning.Layer-6 (Presentation Layer)
In Layer-6 we find, for example, data compression and encryption as well as the implementation of the representation of the data for syntactically correct representation on different systems.Layer-7 (Application Layer)
This is where all end-user applications and services are found (web browser, mail, instant messaging, etc.) as well as network management. Files are also created and output takes place on Layer-7.So much for the structure of the OSI model. This should help you to locate where what is happening in network traffic and provides the first basis for understanding TCP/IP (which will also follow here).
[~] BACK