- Windows
- macOS
- Linux
- Unix
====
Installation:
macOS
shell
brew install nmap
Linux (Ubuntu / Debian):
shell
sudo apt-get install nmap
Windows (.exe):
https://nmap.org/download.html
====
Usage:
shell
$ nmap -h
What can you use nmap for?
Nmap is primarily a port scanner, i.e. nmap checks the running protocols of a domain that you give nmap to see if they are available. Ports are, as already mentioned, protocols and parts of a network address that handle the assignment of TCP and UDP connections and data packets between server and client. Each connection always has two identical ports, one on the server and one on the client side. Ports therefore serve as a feature to distinguish between multiple connections between the same pair of endpoints and ports can identify network protocols and services. A list of all standardized ports can be found here:https://de.wikipedia.org/wiki/Liste_der_standardisierten_Ports
If you want to play around yourself, you can
shell
nmap -h
Display the list of all options and parameters.
====
Simple port scan
The simplest scan variant of nmap is:shell
nmap 127.0.0.1
and it produces the following output:
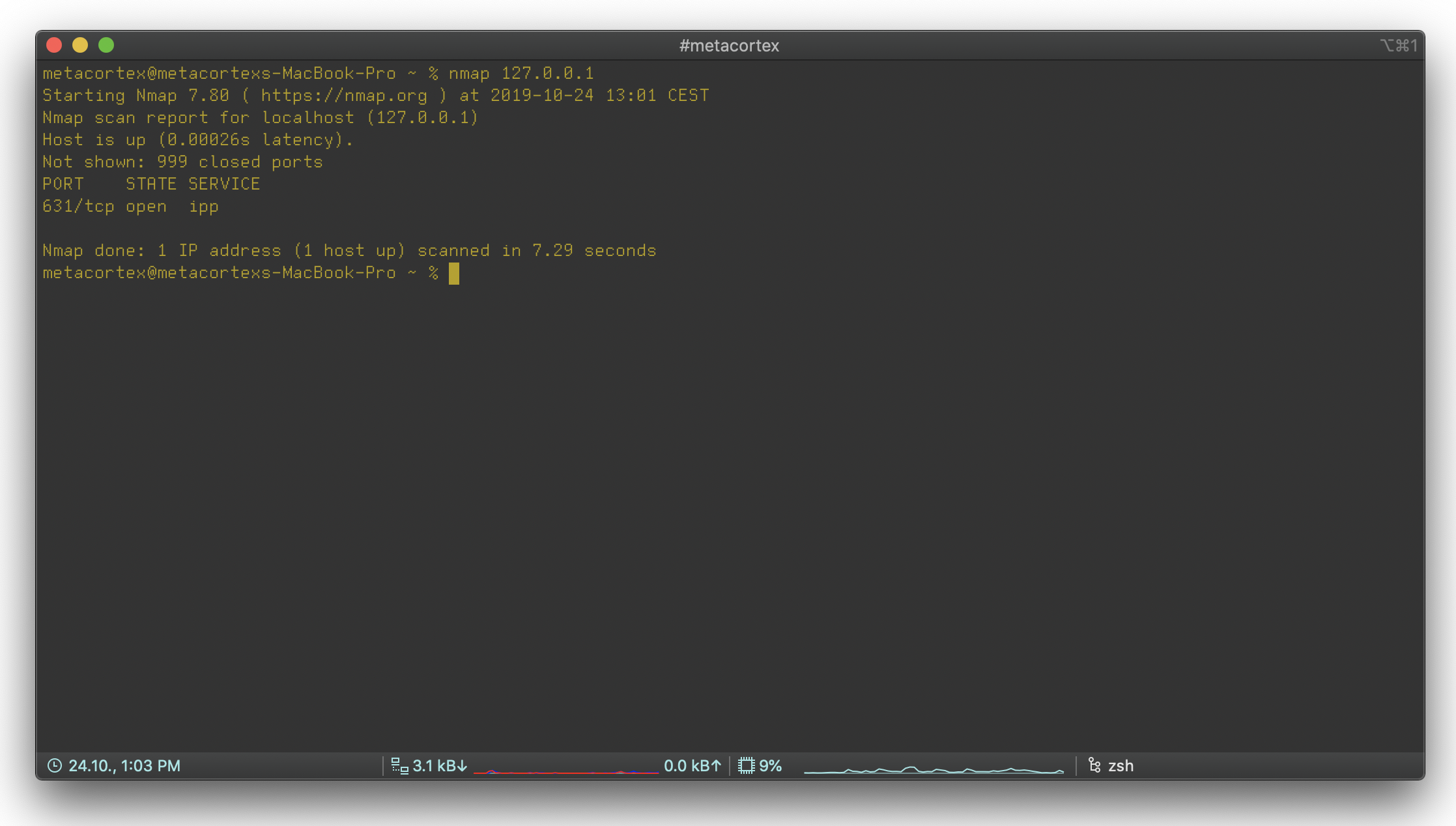
output
Host is up (0.00026s latency)
This means that the scanned host responded and took 0.00026 seconds to do so.
output
Not shown: 999 closed Ports
999 ports are not displayed because they are not open
output
631/TCP open ipp
Port 631 is open and is used by the IPP service. IPP is a printing service provided over the network.
====
Definition of targets
Lines of a scan with nmap can be IP addresses (e.g. 127.0.0.1), hostnames (www.nerdbude.com), network ranges (127.0.0.1-255) and so on. If there are several target systems to be scanned, there are also various parameters that you can give nmap:-iL (processes a file with a list of destinations)
-iR (selects a random number of targets)
--exclude host1[,host2]... (ignores the defined goals)
--excludefile filename (ignores the targets in the passed file)
====
Definition of ports
Similar to the targets, the ports that should be scanned can also be defined.-p (scans only certain ports (z.B. -p22 / -p1-65535 usw.)
--exclude-ports (excludes defined ports from the scan)
-F (Fast-Mode / Scans only the first 100 ports)
-r (Scans ports one by one, not in a random order)
====
Scans
After we have defined our targets and the port, the scanning can begin.shell
nmap -sn 127.0.0.1
Just ping the target and see if it responds and is online
shell
nmap -p1-65535 127.0.0.1
Scans the target for all 65535 existing ports and their state.
shell
nmap -PO [Protocollist] 127.0.0.1
Only scans IP protocol services running on the target.
shell
nmap -O 127.0.0.1
This parameter activates the OS (Operating System) check, so that at the end of the scan the OS used is eliminated.
These are just a few scan options that nmap offers, but they should be a start and a basic understanding. If you want the full list of current parameters and options, you can find them here:
https://nmap.org/data/nmap.usage.txt
and the nmap page is here:
https://nmap.org
[~] BACK